The Essential Role of DMARC in Enhancing Business Email Security
Keeping Your Emails Safe & Building Trust with DMARC!
Email remains a primary communication tool for businesses worldwide, but it is also a significant vector for cyber threats.
In todays world phishing emails account for nearly 70% of all cyber attacks with around 3.4 Billion malicious emails sent every day.
To combat these threats, organisations are increasingly adopting Domain-based Message Authentication, Reporting & Conformance (DMARC). In this blog, i will try to provide an overview of DMARC , its critical role in business security, how historical complexities have driven the adoption of modern platforms like Sendmarc to simplify its use, and the global impact of widespread DMARC adoption.
What Is DMARC?
DMARC (Domain-based Message Authentication, Reporting & Conformance) is a vital tool for keeping your email safe and trustworthy. Its an email authentication protocol that builds on two existing mechanism's, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Imagine you receive an email that looks like it's from Microsoft, but it’s actually a scam. DMARC helps prevent this kind of trickery by making sure emails claiming to be from your domain are actually legitimate.
Example provided by our partner MESH Security
DMARC allows the owner of a domain (like yourcompany.com) to set rules about which emails are genuine and what to do with the ones that aren’t. This means that if someone tries to send a fake email pretending to be from your domain, it gets blocked or flagged.
For those that like a little technical insight, the core components of DMARC as follows and ultimately how the protection works.
1. Defining Your Policies and Publication
- With DMARC Record creation the domain owner, MSP or IT Team, creates a DMARC policy and publishes it in the DNS as a TXT record.
This policy includes:
- The desired action for emails that fail authentication checks (do nothing, quarantine, reject).
- Reporting addresses for aggregate and forensic reports.
- The alignment criteria for SPF and DKIM.
- Example DMARC record:
_dmarc.example.com. IN TXT "v=DMARC1; p=reject; rua=mailto:dmarc-reports@example.com; ruf=mailto:dmarc-forensic@example.com; sp=none; aspf=r; adkim=r"
2. Email Transmission and Authentication
- SPF and DKIM Checks are performed when an email is sent, the receiving mail server performs SPF and DKIM checks:
- SPF verifies that the email is sent from an IP address authorised to send mail for the domain.
- DKIM verifies that the email has not been altered during transit and is signed with a valid key published by the sender's domain.
3. Ensuring DMARC Alignment
- DMARC ensures that the domain in the "From" address matches the domains authenticated by SPF and DKIM. There are two types of alignment:
- Strict Alignment where the domain in the "From" address must exactly match the domain authenticated by SPF or DKIM.
- Relaxed Alignment where the domain in the "From" address must be a subdomain of the domain authenticated by SPF or DKIM.
4. Policy Enforcement
- Depending on the DMARC policy specified, the receiving mail server will take one of the following actions if the email fails SPF and DKIM checks:
- None: No specific action is taken, but reports are sent to the domain owner.
- Quarantine: The email is marked as suspicious and placed in the spam/junk folder.
- Reject: The email is rejected and not delivered to the recipient.
5. Reporting
- Aggregate Reports (RUA) provide a summary of DMARC activity, including the number of emails that passed or failed DMARC checks, sent to the address specified in the "rua" tag.
- Forensic Reports (RUF) provide detailed information about each individual email that failed DMARC checks, sent to the address specified in the "ruf" tag.
6. Continuous Improvement
- Through policy adjustment based on the reports received, domain owners and IT teams can adjust their DMARC policy to improve email authentication and reduce false positives.
- Monitoring and Analysis of DMARC reports helps domain owners and IT Teams identify and mitigate potential security threats, refine their email authentication strategies, and ensure compliance with their DMARC policy.

Source: https://sendmarc.com/10-5-trillion-reasons-why-anti-spam-is-not-enough/
The Challenges in DMARC Implementation
Despite its many benefits, when DMARC was introduced, many businesses were hesitant to adopt it. The primary reason was fear of the unknown. Implementing DMARC requires changes to existing email systems, and businesses were wary of potential disruptions.
Moreover, the technical nature of DMARC made it intimidating for those not well-versed in email security.
For businesses that decided to take the plunge, technical challenges quickly surfaced. Setting up DMARC involves configuring DNS records and ensuring alignment with existing email protocols like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). These tasks often require expertise that smaller businesses lack, leading to misconfigurations and ineffective implementations.
Not to mention that once DMARC is in place, it requires ongoing attention. Managing and interpreting the reports can be time-consuming, demanding regular monitoring and adjustments to ensure everything runs smoothly.
As of 2024, the adoption of DMARC among companies varies significantly. Approximately 43.4% of large organisations have implemented a DMARC policy at the enforcement level, meaning they are actively using DMARC to protect against email spoofing and phishing attacks.
However, the broader adoption rate is much lower. Only about 14% of all domains worldwide are protected from spoofing by an enforcement policy, which indicates that many organisations still have not fully adopted DMARC or are using it without enforcement.
This discrepancy highlights the ongoing challenges and the need for increased awareness and implementation of DMARC policies to improve email security.
The adoption rates vary by industry and region, with some sectors like the U.S. federal government showing higher adoption rates (74%) compared to others, such as global media companies and healthcare companies, which have lower rates of DMARC deployment.
Source: (WebinarCare) (Help Net Security)
Why DMARC adoption is so important!
For companies, implementing DMARC is crucial not just for protecting against cyber threats but also for improving email deliverability and maintaining brand integrity.
Using DMARC helps build trust and removes the risk of domain name impersonation. When people see an email from your company, they can be confident it’s really from you and not a scammer. Because of this, emails are less likely to to be marked as spam, ensuring critical communications reach their intended recipients. DMARC gives you reports that show you how your domain is being used, so you can spot any suspicious activity and stop it in its tracks.
Not to mention with increasing regulations around data protection and cybersecurity, implementing DMARC helps businesses comply with legal requirements, reducing the risk of penalties and enhancing their overall security posture.
A key way DMARC supports businesses is through its comprehensive reporting. Once DMARC is enabled on a domain, it allows email receivers to generate detailed Aggregate and Forensic Reports, providing valuable insights into your email security.
In short, DMARC is like a security guard for your email, protecting your brand and your customers from fraud and keeping your communications safe and reliable.
The following infographic shows the impact of email based cyber crime to further compound the need for business to adopt solutions such as DMARC.
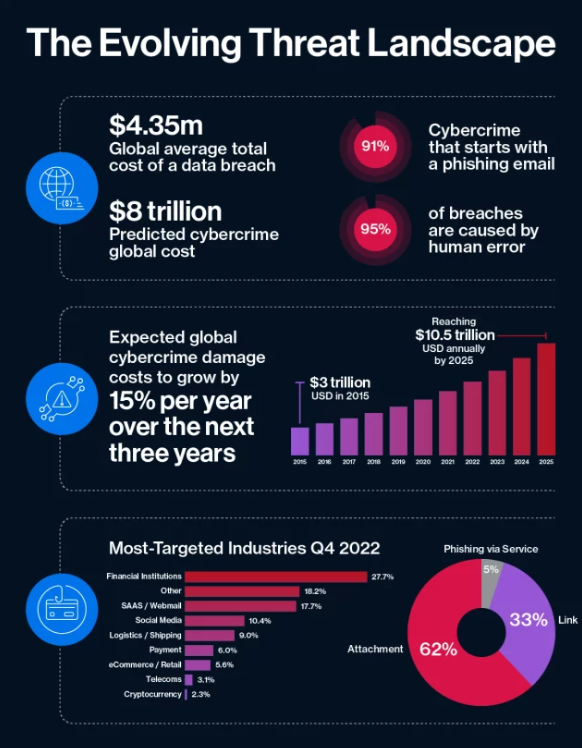
Source: https://sendmarc.com/10-5-trillion-reasons-why-anti-spam-is-not-enough/
The Future of Email Security with DMARC
With evolving threats and the need for continuous improvement it's crucial for organisations to stay ahead by continuously improving their email security measures. This includes regularly updating DMARC policies and staying informed about new threats.
But also consider DMARC as a tool in your email and domain defensive arsenal. It is most effective when integrated with other security technologies, such as advanced threat protection, secure email gateways, and AI-based anomaly detection systems, but is still equally as powerful when used on its own.
The email security community is continually working on enhancing DMARC and related protocols including the introduction of DMARC management platforms like our own partner Sendmarc, who are revolutionising the way businesses implement and manage DMARC.
These platforms are empowering IT Teams and MSP's with the tools required to stay a step ahead of cyber criminals by having a clear view of their email systems and potential threats.
Partnering with Sendmarc was a strategic decision taken by ourselves. We wanted to provide our clients with the best possible defense against email threats and the visibility and control offered by Sendmarc has been game-changer. They allow us to monitor, analyse, and respond to email security issues with unprecedented efficiency and is now a tool we wouldn't be without.
A final Note
Cybersecurity has become an essential focus for businesses of all sizes. The increasing frequency and sophistication of cyber threats make
it clear that protecting sensitive data and maintaining the integrity of digital operations is no longer optional but a necessity.
For business owners, understanding and implementing effective cybersecurity measures should be at the forefront of strategic planning.
The sheer choice of security technologies is vast and constantly evolving. From firewalls and antivirus software to more advanced solutions like AI-driven threat detection and response systems, the array of options can be overwhelming. This abundance of choices often leads to two problematic mindsets, either believing that cybersecurity is irrelevant to one's business or feeling paralysed by the complexity of selecting the right tools and providers.
Email remains a critical communication tool for businesses so ensuring its security has got to be part of any businesses security strategy. Business that implement DMARC and adopt DMARC reporting tools, can efficiently prevent email impersonation, maintain brand trust and safeguard your clients from email-based cyber attacks, whilst also protecting your own business.
However, while DMARC is crucial and we believe that all business should adopt it's use, it should not be the sole focus of an email security strategy. A layered approach is essential, combining DMARC with advanced email filtering services that can detect and block a wide range of email based threats. This broader, integrated security strategy ensures comprehensive protection and minimises the risk of successful cyber attacks.
If you would like to find out more about our DMARC and other services myself and my team are on hand to answer any questions and transform a daunting task into a manageable, strategic advantage. contact us today.








